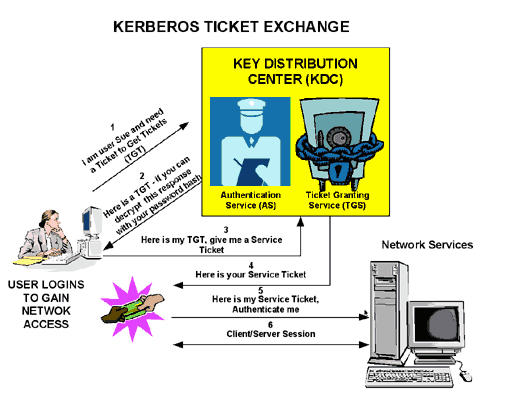
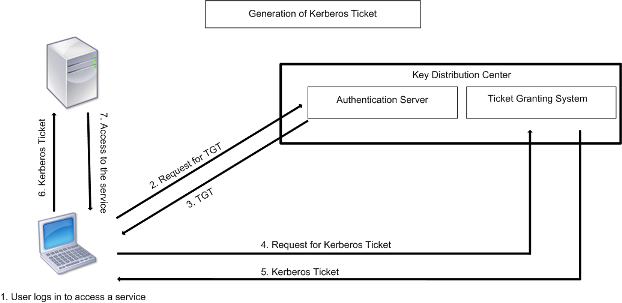
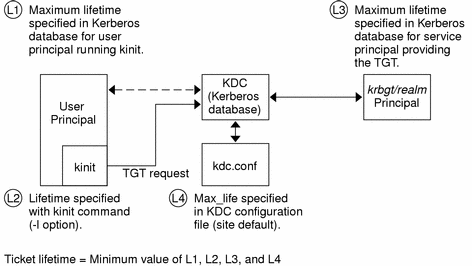
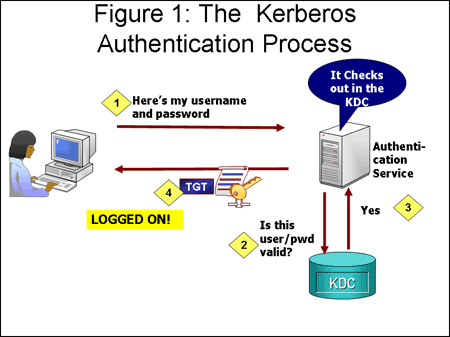
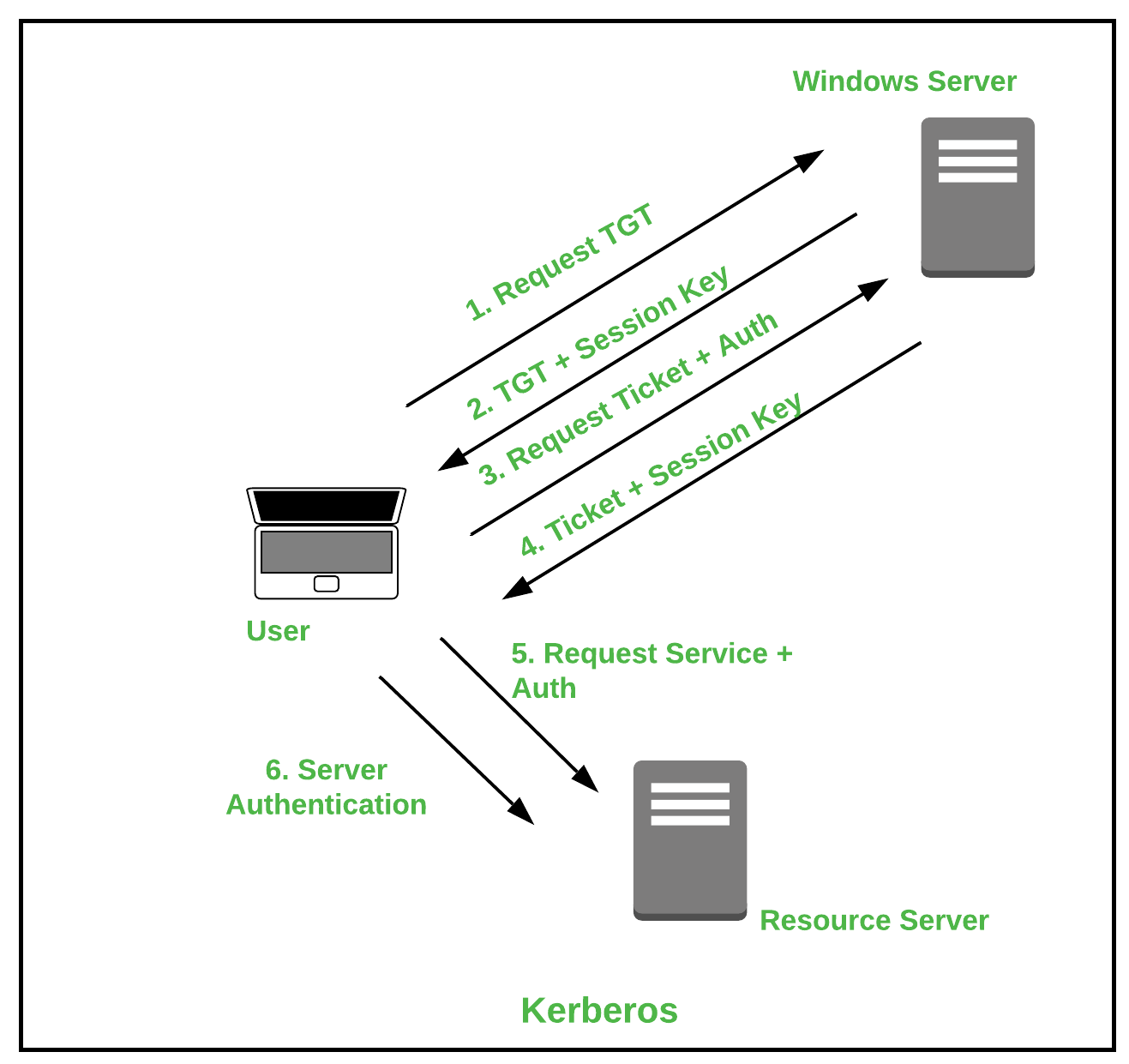
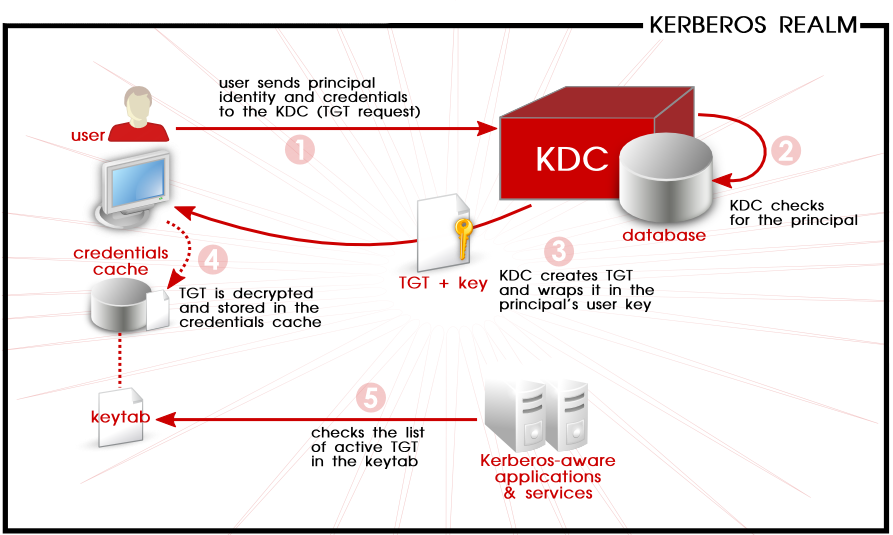
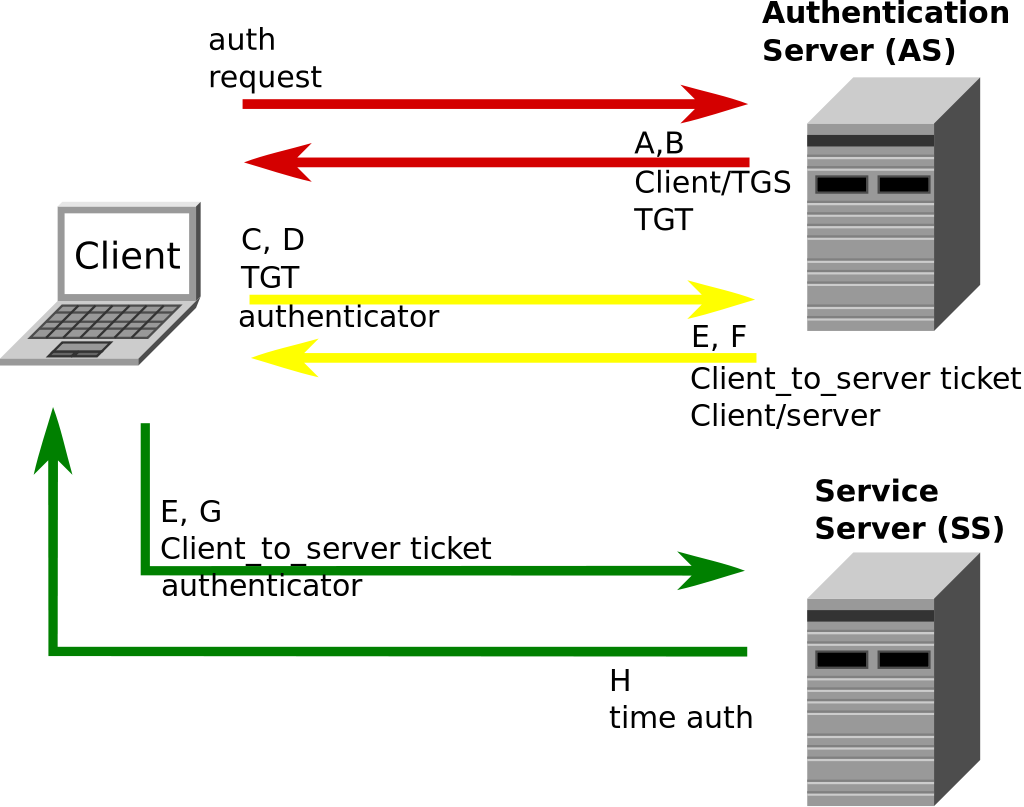
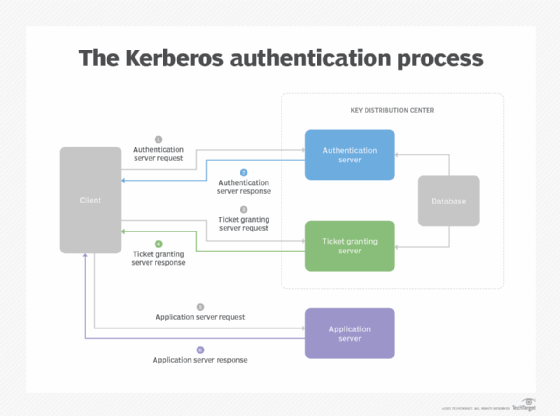
An Overview of Authentication for Computer Communications – Page 3 – A Quarterly Publication of ACCS

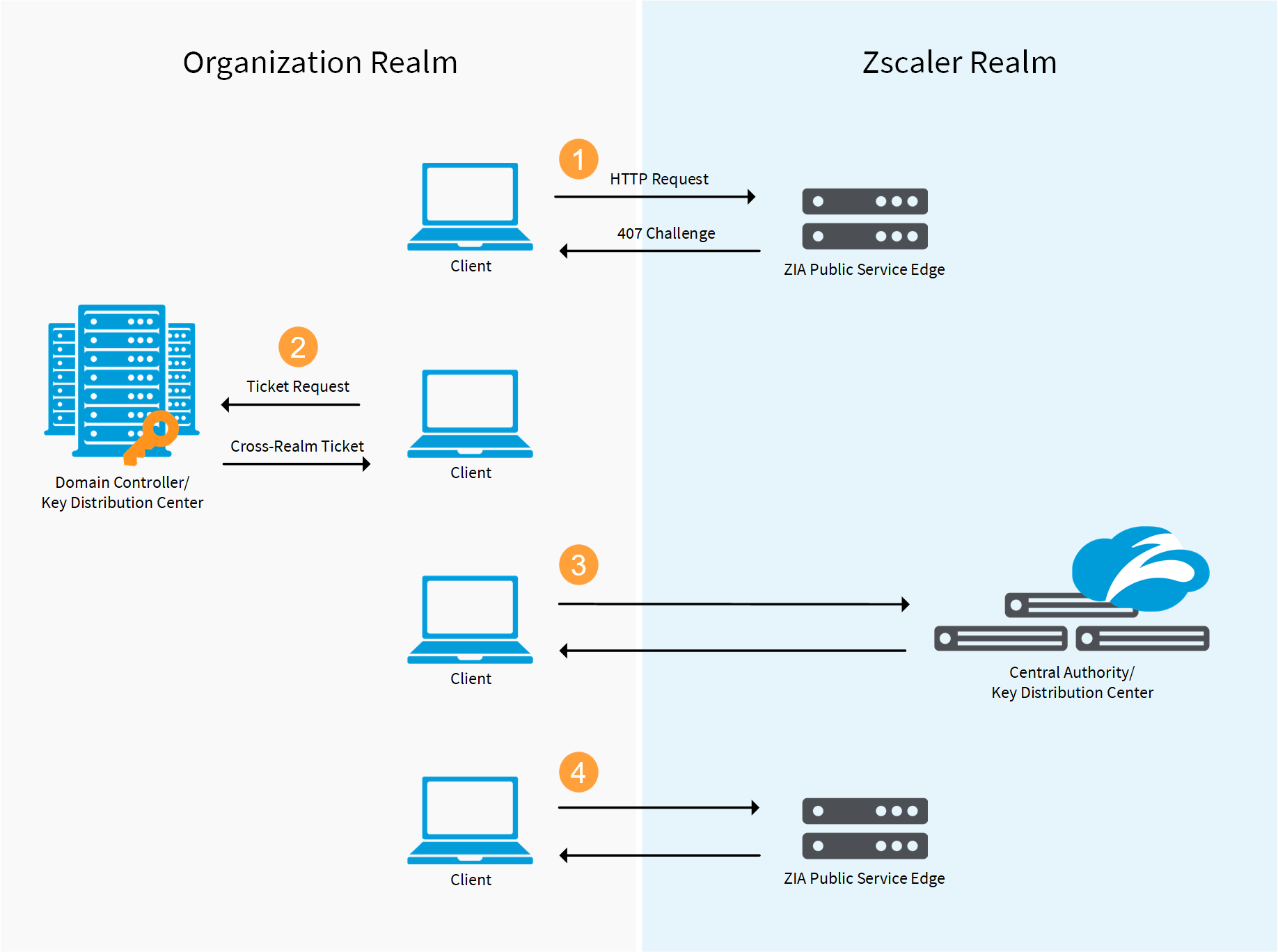
Kerberos Authentication for Hadoop Ÿ The Kerberos delegated external... | Download Scientific Diagram

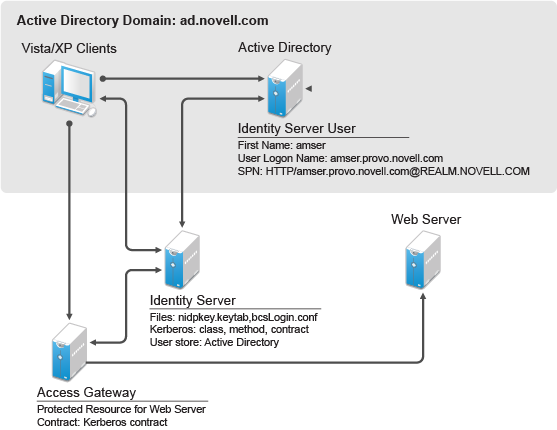
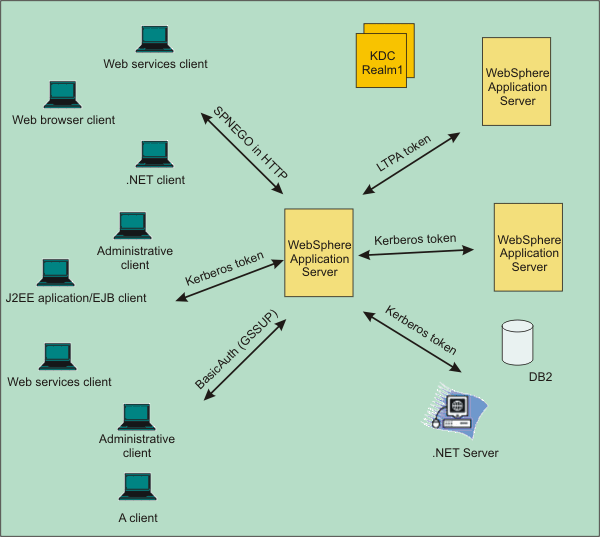
Novell Doc: Novell Access Manager 3.0 SP4 Administration Guide - Configuring Kerberos for Authentication