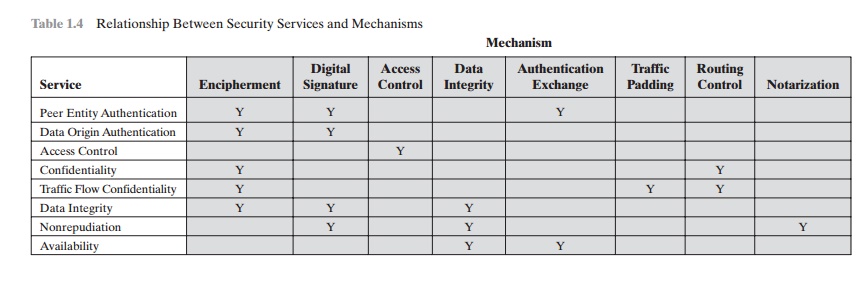
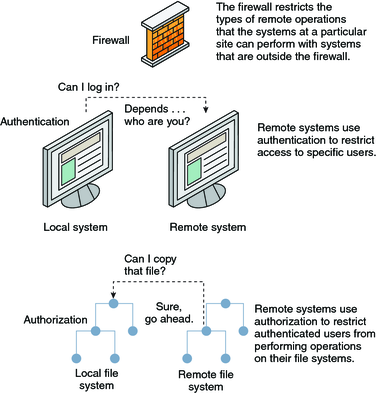
Cryptography and Security Services: Mechanisms and Applications: Manuel Mogollon: 9781599048376: Books: Amazon.com

General Security and Privacy Mechanisms for Liberty Identity Web Services Framework | Protogenist Blog

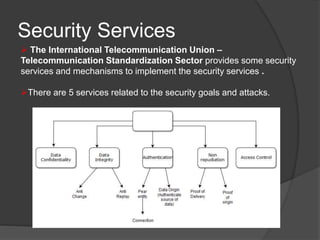
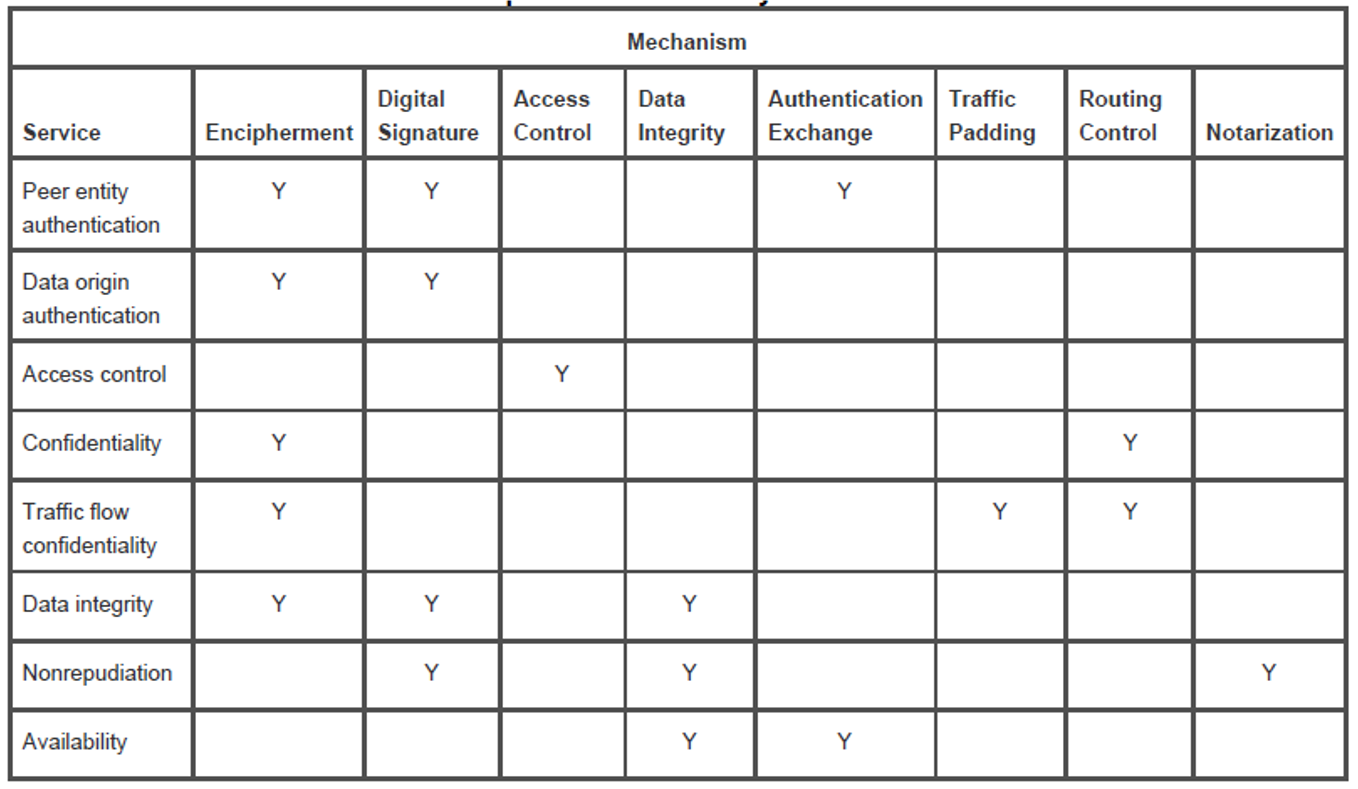
Henric Johnson1 Network Security /. 2 Outline Attacks, services and mechanisms Security attacks Security services Methods of Defense A model for Internetwork. - ppt download